IntoDNS checks the health and configuration and provides DNS report and mail servers report.And provides suggestions to fix and improve them, with references to protocols’ official documentation.
Blog
-
intoDNS: checks DNS and mail servers health
-
TV election debates create ‘plausible tarts’, warns historian
Peter Hennessy said that he had “grave reservations†about the broadcasting of the leadership debates, which took place in Britain for the first time before the 2010 Âgeneral election.
Warning that they meant future leaders would be selected for being “plausible tarts†rather than simply “decentâ€, he said a culture of “celebritocracy†could blight politics.
Lord Hennessy, a cross-bench peer, added that Clement Attlee, the post-war Labour prime minister, would never be elected today because his “considerable virtues†would be eclipsed by his “charisma and presence of a gerbilâ€.
“The problem with the debates is that the structure of them, the nature of the celebrity in Britain in parts of the media these days, mean that to shine in leadership debates before a general election, you need the characteristics of a plausible tart,†he said.
“Now, being a plausible tart is about 10 per cent of the requirement of being prime minister — no more. It’s not the most important bit.
“My fear is that we’ll be stuck with these leadership elections and when parties choose leaders in the future, the plausible tart bit will play too powerfully in their choice of leader and therefore rule out the decent but non-tarty people.â€
“They’re only happy in their own company.
Speaking of the perils of 24-hour news, Lord Hennessy also criticised the habit of parties to rush into responses and “collapse in tittishness†by posting reactions to everything on Twitter.
“The cumulative power of celebritocracy and soundbitery means that it’s an ever narrower spectrum in which you operate,†he said.
“Clement Attlee wouldn’t get through any selection process now because his answers would be monosyllabic.
“He was a man of considerable virtue but it would be unimaginable today, because he had all the charisma and presence of a gerbil. It’s inconceivable now. If there was such a character around, he or she wouldn’t make it.â€
via Ways With Words 2013: TV election debates create ‘plausible tarts’, warns historian – Telegraph.
-
Robert Douglas of Ribot – Designing for multiple platforms on Vimeo
Robert Douglas of Ribot – Designing for multiple platforms
via Robert Douglas of Ribot – Designing for multiple platforms on Vimeo.
-
HP laserjet P1102W wifi setup fail
Here’s an unofficial but quite professional screencast showing how it should work:
First I try to connect to the printer network:
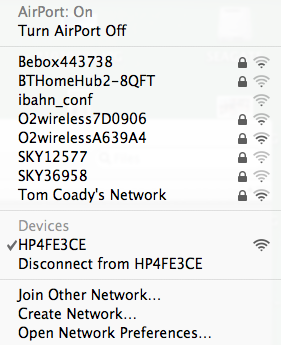
Connect to P1102W network Then I try opening the print setup:

Then Print Utility
 and nothing happens apart from the OSX lit up click lamp on the button.which I tried despite the fact that the open printer utility fails (it should launch a web page hosted by the printer itself).
and nothing happens apart from the OSX lit up click lamp on the button.which I tried despite the fact that the open printer utility fails (it should launch a web page hosted by the printer itself).This is the start of the problem: it never seems to know where it is, or if it does it won’t volunteer this information using the Bonjour protocol by default, but it’s address does appear in tcpdump when connected to its own “device” network:
What happens when settings applied Connect to P1102W network Wireless settings default Network settings required Network settings defaults printer settings open print utility The official way to find this out is via by printing out a test page. The address assigned is always on the 169 subnet and keeps changing. When I apply the changes to the wireless alone or the wireless and what are the correct network settings together it goes in to a hanging mode where the printout shows it has attached itself to my network but its address is still on the 169 subnet and it’s using its own dhcp.
One last thing to try might be to set my own network to the same as this but as there are at several other devices on 192 I’m reluctant to even try that out.
Configuration printouts
configuration print outs to pdf
tcpdump
Tom-Coadys-MacBook-Pro:~ tomxcoady$ sudo tcpdump -i en1
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on en1, link-type EN10MB (Ethernet), capture size 65535 bytes
16:37:56.902414 ARP, Request who-has 169.254.87.142 tell 0.0.0.0, length 46
16:37:57.780097 IP tom-coadys-macbook-pro.local.mdns > 224.0.0.251.mdns: 0 PTR (QM)? 142.87.254.169.in-addr.arpa. (45)
16:37:57.780429 IP6 tom-coadys-macbook-pro.local.mdns > ff02::fb.mdns: 0 PTR (QM)? 142.87.254.169.in-addr.arpa. (45)
16:37:58.781839 IP tom-coadys-macbook-pro.local.mdns > 224.0.0.251.mdns: 0 PTR (QM)? 142.87.254.169.in-addr.arpa. (45)
16:37:58.782079 IP6 tom-coadys-macbook-pro.local.mdns > ff02::fb.mdns: 0 PTR (QM)? 142.87.254.169.in-addr.arpa. (45)
16:37:58.892288 ARP, Request who-has 169.254.87.142 tell 0.0.0.0, length 46
16:38:00.882314 ARP, Request who-has 169.254.87.142 tell 0.0.0.0, length 46
16:38:01.948848 IP 0.0.0.0.bootpc > broadcasthost.bootps: BOOTP/DHCP, Request from 00:23:6c:83:16:a4 (oui Unknown), length 300
16:38:02.871973 ARP, Request who-has 169.254.87.142 tell 0.0.0.0, length 46
16:38:03.212434 IP 0.0.0.0.bootpc > broadcasthost.bootps: BOOTP/DHCP, Request from 00:23:6c:83:16:a4 (oui Unknown), length 300
16:38:05.382180 IP 0.0.0.0.bootpc > broadcasthost.bootps: BOOTP/DHCP, Request from 00:23:6c:83:16:a4 (oui Unknown), length 300
16:38:06.852627 ARP, Request who-has 169.254.87.142 tell 169.254.87.142, length 46
16:38:08.846282 ARP, Request who-has 169.254.87.142 tell 169.254.87.142, length 46
16:38:09.568499 IP6 fe80::f6ce:46ff:fe4f:e3ce > ff02::1:ff4f:e3ce: HBH ICMP6, multicast listener reportmax resp delay: 0 addr: ff02::1:ff4f:e3ce, length 24
16:38:09.570396 IP6 :: > ff02::1:ff4f:e3ce: ICMP6, neighbor solicitation, who has fe80::f6ce:46ff:fe4f:e3ce, length 24
16:38:09.571402 IP6 fe80::f6ce:46ff:fe4f:e3ce > ff02::2: ICMP6, router solicitation, length 8
16:38:09.767804 IP 0.0.0.0.bootpc > broadcasthost.bootps: BOOTP/DHCP, Request from 00:23:6c:83:16:a4 (oui Unknown), length 300
16:38:09.822698 IP tom-coadys-macbook-pro.local.mdns > 224.0.0.251.mdns: 0 PTR (QM)? e.c.3.e.f.4.e.f.f.f.6.4.e.c.6.f.0.0.0.0.0.0.0.0.0.0.0.0.0.8.e.f.ip6.arpa. (90)
16:38:09.822795 IP6 tom-coadys-macbook-pro.local.mdns > ff02::fb.mdns: 0 PTR (QM)? e.c.3.e.f.4.e.f.f.f.6.4.e.c.6.f.0.0.0.0.0.0.0.0.0.0.0.0.0.8.e.f.ip6.arpa. (90)
16:38:09.837470 IP6 fe80::f6ce:46ff:fe4f:e3ce.dhcpv6-client > ff02::1:2.dhcpv6-server: dhcp6 solicit
16:38:13.499378 IP6 tom-coadys-macbook-pro.local.mdns > ff02::fb.mdns: 0 [5a] [15q] PTR (QM)? _afpovertcp._tcp.local. PTR (QM)? _smb._tcp.local. PTR (QM)? _rfb._tcp.local. PTR (QM)? _adisk._tcp.local. PTR (QM)? _see._tcp.local. PTR (QM)? _daap._tcp.local. PTR (QM)? _appletv-pair._tcp.local. PTR (QM)? _appletv._tcp.local. PTR (QM)? _00000000-03d9-f72b-4ca8-f84b129d4330._sub._appletv-v2._tcp.local. PTR (QM)? _00000000-03d9-f72b-4ca8-f84b129d4330._sub._home-sharing._tcp.local. PTR (QM)? _touch-remote._tcp.local. PTR (QM)? _raop._tcp.local. PTR (QM)? _airplay._tcp.local. SRV (QM)? HP LaserJet Professional P1102w._riousbprint._tcp.local.._http._tcp.local. TXT (QM)? HP LaserJet Professional P1102w._riousbprint._tcp.local.._http._tcp.local. (585)
16:38:13.547869 IP6 fe80::f6ce:46ff:fe4f:e3ce > ff02::2: ICMP6, router solicitation, length 8
16:38:14.546318 IP 169.254.87.142 > 239.255.255.250: igmp v2 report 239.255.255.250
16:38:14.547427 IP6 fe80::f6ce:46ff:fe4f:e3ce > ff02::c: HBH ICMP6, multicast listener reportmax resp delay: 0 addr: ff02::c, length 24
16:38:14.762537 IP 169.254.87.142.upnp-discovery > 239.255.255.250.upnp-discovery: UDP, length 1281
16:38:14.782386 IP 169.254.87.142.upnp-discovery > 239.255.255.250.upnp-discovery: UDP, length 1281
16:38:14.815985 IP 169.254.87.142 > 224.0.1.60: igmp v2 report 224.0.1.60
16:38:14.816952 IP6 fe80::f6ce:46ff:fe4f:e3ce > ff02::116: HBH ICMP6, multicast listener reportmax resp delay: 0 addr: ff02::116, length 24
16:38:14.818064 IP6 fe80::f6ce:46ff:fe4f:e3ce > ff02::fb: HBH ICMP6, multicast listener reportmax resp delay: 0 addr: ff02::fb, length 24
16:38:14.852390 IP6 fe80::f6ce:46ff:fe4f:e3ce.upnp-discovery > ff02::c.upnp-discovery: UDP, length 1281
16:38:18.164147 IP 0.0.0.0.bootpc > broadcasthost.bootps: BOOTP/DHCP, Request from 00:23:6c:83:16:a4 (oui Unknown), length 300
16:38:19.799281 IP 169.254.87.142.mdns > 224.0.0.251.mdns: 0 [6q] [6n] ANY (QM)? NPI4FE3CE.local. ANY (QM)? NPI4FE3CE.local. ANY (QM)? HP LaserJet Professional P1102w._pdl-datastream._tcp.local. ANY (QM)? HP LaserJet Professional P1102w._http._tcp.local. ANY (QM)? HP LaserJet Professional P1102w._http-alt._tcp.local. ANY (QM)? HP LaserJet Professional P1102w._printer._tcp.local. (361)
16:38:19.803338 IP6 fe80::f6ce:46ff:fe4f:e3ce.mdns > ff02::fb.mdns: 0 [6q] [6n] ANY (QM)? NPI4FE3CE.local. ANY (QM)? NPI4FE3CE.local. ANY (QM)? HP LaserJet Professional P1102w._pdl-datastream._tcp.local. ANY (QM)? HP LaserJet Professional P1102w._http._tcp.local. ANY (QM)? HP LaserJet Professional P1102w._http-alt._tcp.local. ANY (QM)? HP LaserJet Professional P1102w._printer._tcp.local. (361)
16:38:20.371449 IP tom-coadys-macbook-pro.local.mdns > 224.0.0.251.mdns: 0*- [0q] 38/0/0 (Cache flush) TXT "", PTR _afpovertcp._tcp.local., PTR Tom CoadyM-bM-^@M-^Ys MacBook Pro._afpovertcp._tcp.local., TXT "model=MacBookPro5,1", (Cache flush) TXT "", PTR _smb._tcp.local., PTR Tom CoadyM-bM-^@M-^Ys MacBook Pro._smb._tcp.local., (Cache flush) TXT "", PTR _ssh._tcp.local., PTR Tom CoadyM-bM-^@M-^Ys MacBook Pro._ssh._tcp.local., (Cache flush) TXT "", PTR _sftp-ssh._tcp.local., PTR Tom CoadyM-bM-^@M-^Ys MacBook Pro._sftp-ssh._tcp.local., (Cache flush) SRV Tom-Coadys-MacBook-Pro.local.:548 0 0, (Cache flush) SRV Tom-Coadys-MacBook-Pro.local.:445 0 0, (Cache flush) SRV Tom-Coadys-MacBook-Pro.local.:22 0 0, (Cache flush) SRV Tom-Coadys-MacBook-Pro.local.:22 0 0, (Cache flush) TXT "sys=waMA=00:23:DF:7C:A1:46,adVF=0x200,adDT=0x3,adCC=1", PTR _odisk._tcp.local., PTR Tom CoadyM-bM-^@M-^Ys MacBook Pro._odisk._tcp.local., (Cache flush) TXT "", PTR _rfb._tcp.local., PTR Tom CoadyM-bM-^@M-^Ys MacBook Pro._rfb._tcp.local., TXT "LKDC:SHA1.9ABB9D91F95F0388A329FF682FF826A158AB6AD7", (Cache flush) SRV Tom-Coadys-MacBook-Pro.local.:49152 0 0, (Cache flush) SRV Tom-Coadys-MacBook-Pro.local.:5900 0 0, (Cache flush) TXT "txtvers=1" "userid=47837200-6C10-44B1-9012-60659F49E5F4" "name=Tom Coady" "version=2", PTR _see._tcp.local., PTR tomxcoady@Tom CoadyM-bM-^@M-^Ys MacBook Pro._see._tcp.local., (Cache flush) SRV Tom-Coadys-MacBook-Pro.local.:6942 0 0, (Cache flush) TXT "txtvers=1" "DbId=EC2F25162B4B504E" "CtlN=Tom CoadyM-bM-^@M-^Ys Library" "OSsi=0x1F6" "DvSv=2577" "DvTy=iTunes" "iV=196612" "Ver=131074", PTR _touch-able._tcp.local., PTR 89503FFFDFF532F5._touch-able._tcp.local., (Cache flush) TXT "txtvers=1" "DbId=EC2F25162B4B504E" "CtlN=Tom CoadyM-bM-^@M-^Ys Library" "OSsi=0x1F6" "msg=" "DvSv=2577" "DvTy=iTunes" "iV=196612" "Ver=131074", PTR _remote-jukebox._tcp.local., PTR 89503FFFDFF532F5._remote-jukebox._tcp.local., PTR _home-sharing._tcp.local., PTR Tom CoadyM-bM-^@M-^Ys Library._home-sharing._tcp.local. (1448)
16:38:42.133646 IP6 fe80::f6ce:46ff:fe4f:e3ce.dhcpv6-client > ff02::1:2.dhcpv6-server: dhcp6 solicit
16:38:43.756270 ARP, Request who-has 192.168.1.254 tell 192.168.1.85, length 28
16:38:52.339011 ARP, Request who-has 192.168.1.254 tell 192.168.1.85, length 28
16:38:57.015542 IP tom-coadys-macbook-pro.local.50887 > 169.254.87.142.http: Flags [S], seq 3051841237, win 65535, options [mss 1460,nop,wscale 3,nop,nop,TS val 997133271 ecr 0,sackOK,eol], length 0
16:38:57.018243 ARP, Request who-has tom-coadys-macbook-pro.local tell 169.254.87.142, length 46
16:38:57.018295 ARP, Reply tom-coadys-macbook-pro.local is-at 00:23:6c:83:16:a4 (oui Unknown), length 28
16:38:57.020959 IP 169.254.87.142.http > tom-coadys-macbook-pro.local.50887: Flags [S.], seq 975060428, ack 3051841238, win 8688, options [mss 1460,nop,nop,sackOK,nop,nop,TS val 194040 ecr 997133271], length 0
16:38:57.021017 IP tom-coadys-macbook-pro.local.50887 > 169.254.87.142.http: Flags [.], ack 1, win 65535, options [nop,nop,TS val 997133271 ecr 194040], length 0
16:39:01.145555 ARP, Request who-has 192.168.1.254 tell 192.168.1.85, length 28
16:39:01.145676 IP 0.0.0.0.bootpc > broadcasthost.bootps: BOOTP/DHCP, Request from 00:23:6c:83:16:a4 (oui Unknown), length 300
16:39:01.160689 ARP, Request who-has 10.105.116.1 tell 10.105.119.19, length 28
16:39:14.061850 IP6 fe80::f6ce:46ff:fe4f:e3ce.dhcpv6-client > ff02::1:2.dhcpv6-server: dhcp6 solicit
16:39:17.024395 IP tom-coadys-macbook-pro.local.50887 > 169.254.87.142.http: Flags [P.], seq 2577:3018, ack 46055, win 65535, options [nop,nop,TS val 997133471 ecr 210780], length 441
HP LaserJet Professional P1102w._printer._tcp.local. (1239)
16:39:28.829295 IP tom-coadys-macbook-pro.local.netbios-dgm > 169.254.255.255.netbios-dgm: NBT UDP PACKET(138)
16:39:29.798610 IP tom-coadys-macbook-pro.local.mdns > 224.0.0.251.mdns: 0 PTR (QM)? 255.255.254.169.in-addr.arpa. (46)
16:39:29.798948 IP6 tom-coadys-macbook-pro.local.mdns > ff02::fb.mdns: 0 PTR (QM)? 255.255.254.169.in-addr.arpa. (46)
16:39:30.801447 IP tom-coadys-macbook-pro.local.mdns > 224.0.0.251.mdns: 0 PTR (QM)? 255.255.254.169.in-addr.arpa. (46)
16:39:30.801681 IP6 tom-coadys-macbook-pro.local.mdns > ff02::fb.mdns: 0 PTR (QM)? 255.255.254.169.in-addr.arpa. (46)
16:39:33.460831 IP tom-coadys-macbook-pro.local.50887 > 169.254.87.142.http: Flags [F.], seq 3370, ack 61883, win 65535, options [nop,nop,TS val 997133635 ecr 214780], length 0
16:39:33.461030 IP tom-coadys-macbook-pro.local.50888 > 169.254.87.142.http: Flags [F.], seq 3124, ack 67503, win 65535, options [nop,nop,TS val 997133635 ecr 214780], length 0
16:40:40.881671 IP tom-coadys-macbook-pro.local.50893 > 169.254.87.142.http: Flags [F.], seq 763, ack 5567, win 65535, options [nop,nop,TS val 997134308 ecr 230690], length 0
16:40:42.840454 IP tom-coadys-macbook-pro.local.netbios-ns > 169.254.255.255.netbios-ns: NBT UDP PACKET(137): REGISTRATION; REQUEST; BROADCAST
16:40:42.895153 IP tom-coadys-macbook-pro.local.netbios-dgm > 169.254.255.255.netbios-dgm: NBT UDP PACKET(138)
16:40:45.547211 IP 0.0.0.0.bootpc > broadcasthost.bootps: BOOTP/DHCP, Request from 00:23:6c:83:16:a4 (oui Unknown), length 300
16:40:53.592388 ARP, Request who-has 10.105.116.1 tell 10.105.119.19, length 28
16:40:53.592431 ARP, Request who-has 192.168.1.254 tell 192.168.1.85, length 28
16:40:53.592556 IP 0.0.0.0.bootpc > broadcasthost.bootps: BOOTP/DHCP, Request from 00:23:6c:83:16:a4 (oui Unknown), length 300
16:40:53.607519 ARP, Request who-has 10.105.116.1 tell 10.105.119.19, length 28
16:40:53.607545 ARP, Request who-has 192.168.1.254 tell 192.168.1.85, length 28
16:40:53.622628 ARP, Request who-has 10.105.116.1 tell 10.105.119.19, length 28
16:40:53.622650 ARP, Request who-has 192.168.1.254 tell 192.168.1.85, length 28 -
Wikileaks evades hackers with shift to Amazon EC2
Wikileaks, the site that has infuriated the US government by releasing thousands of US diplomatic cables, is being hosted by one of the symbols of that country’s internet success – Amazon.
The site came under a “Distributed Denial of Service” (DDOS) attack on Sunday night from an unidentified hacker, forcing it to seek a new location for its computer files. And it found it though Amazon’s “Elastic Cloud Computing” (EC2) service, which enables businesses to hire its servers and store their data there.
DDOS attacks typically force sites off the net unless they have enormous bandwidth at their disposal or highly effective countermeasures. Wikileaks, being small and struggling for funds, is neither.
But EC2 allows companies to pay for their usage as it mounts up, rather than upfront.
While Amazon is American, not all of its servers are hosted there – and it could cause a major incident if the US government were to take action against a company on the basis that it might be hosting material the government finds embarrassing.
via Wikileaks evades hackers with shift to Amazon | Media | guardian.co.uk.
-
One example of Twitter’s excellent UX
Brilliant example of Twitter’s idiot proof design :
Sorry, ignore the highlighted words – I was using that as a lazy way to post this blog using the excellent Press This WordPress bookmarklet, and the tweet itself was lazily created the same way. FWIW I resent the tweet as the first attempt resulted in a fairly dire server busy error. Maybe its that unreliability that inspired the sanity check loop?
-
15 reasons why twitter threatens the old 4th estate
15 things that Twitter does rather effectively and which should be of the deepest interest to anyone involved in the media at any level.
1. It’s an amazing form of distribution
It’s a highly effective way of spreading ideas, information and content. Don’t be distracted by the 140-character limit. A lot of the best tweets are links. It’s instantaneous. Its reach can be immensely far and wide. Why does this matter? Because we do distribution too. We’re now competing with a medium that can do many things incomparably faster than we can. It’s back to the battle between scribes and movable type. That matters in journalistic terms. And, if you’re trying to charge for content, it matters in business terms. The life expectancy of much exclusive information can now be measured in minutes, if not in seconds. That has profound implications for our economic model, never mind the journalism.
2. It’s where things happen first
Not all things. News organisations still break lots of news. But, increasingly, news happens first on Twitter. If you’re a regular Twitter user, even if you’re in the news business and have access to the wires, the chances are that you’ll check out many rumours of breaking news on Twitter first. There are millions of human monitors out there who will pick up on the smallest things and who have the same instincts as the agencies – to be the first with the news. As more people join, the better it will get.
3. As a search engine, it rivals Google
Many people still don’t quite understand that Twitter is, in some respects, better than Google in finding stuff out. Google is limited to using algorithms to ferret out information in the unlikeliest hidden corners of the web. Twitter goes one stage further – harnessing the mass capabilities of human intelligence to the power of millions in order to find information that is new, valuable, relevant or entertaining.
4. It’s a formidable aggregation tool
You set Twitter to search out information on any subject you want and it will often bring you the best information there is. It becomes your personalised news feed. If you are following the most interesting people they will in all likelihood bring you the most interesting information. In other words, it’s not simply you searching. You can sit back and let other people you admire or respect go out searching and gathering for you. Again, no news organisation could possibly aim to match, or beat, the combined power of all those worker bees collecting information and disseminating it.
5. It’s a great reporting tool
Many of the best reporters are now habitually using Twitter as an aid to finding information. This can be simple requests for knowledge that other people already know, have to hand, or can easily find. The so-called wisdom of crowds comes into play: the “they know more than we do” theory. Or you’re simply in a hurry and know that someone out there will know the answer quickly. Or it can be reporters using Twitter to find witnesses to specific events – people who were in the right place at the right time, but would otherwise be hard to find.
6. It’s a fantastic form of marketing
You’ve written your piece or blog. You may well have involved others in the researching of it. Now you can let them all know it’s there, so that they come to your site. You alert your community of followers. In marketing speak, it drives traffic and it drives engagement. If they like what they read they’ll tell others about it. If they really like it, it will, as they say, “go viral”. I only have 18,500 followers. But if I get retweeted by one of our columnists, Charlie Brooker, I reach a further 200,000. If Guardian Technology picks it up it goes to an audience of 1.6 million. If Stephen Fry notices it, it’s global.
7. It’s a series of common conversations
Or it can be. As well as reading what you’ve written and spreading the word, people can respond. They can agree or disagree or denounce it. They can blog elsewhere and link to it. There’s nothing worse than writing or broadcasting something to no reaction at all. With Twitter you get an instant reaction. It’s not transmission, it’s communication. It’s the ability to share and discuss with scores, or hundreds, or thousands of people in real time. Twitter can be fragmented. It can be the opposite of fragmentation. It’s a parallel universe of common conversations.
8. It’s more diverse
Traditional media allowed a few voices in. Twitter allows anyone.
9. It changes the tone of writing
A good conversation involves listening as well as talking. You will want to listen as well as talk. You will want to engage and be entertaining. There is, obviously, more brevity on Twitter. There’s more humour. More mixing of comment with fact. It’s more personal. The elevated platform on which journalists sometimes liked to think they were sitting is kicked away on Twitter. Journalists are fast learners. They start writing differently.
Talking of which …
10. It’s a level playing field
A recognised “name” may initially attract followers in reasonable numbers. But if they have nothing interesting to say they will talk into an empty room. The energy in Twitter gathers around people who can say things crisply and entertainingly, even though they may be “unknown”. They may speak to a small audience, but if they say interesting things they may well be republished numerous times and the exponential pace of those re-transmissions can, in time, dwarf the audience of the so-called big names. Shock news: sometimes the people formerly known as readers can write snappier headlines and copy than journalists can.
11. It has different news values
People on Twitter quite often have an entirely different sense of what is and what isn’t news. What seems obvious to journalists in terms of the choices we make is quite often markedly different from how others see it – both in terms of the things we choose to cover and the things we ignore. The power of tens of thousands of people articulating those different choices can wash back into newsrooms and affect what editors choose to cover. We can ignore that, of course. But should we?
12. It has a long attention span
The opposite is usually argued – that Twitter is simply an instant, highly condensed stream of consciousness. The perfect medium for goldfish. But set your TweetDeck to follow a particular keyword or issue or subject and you may well find that the attention span of Twitter users puts newspapers to shame. They will be ferreting out and aggregating information on the issues that concern them long after the caravan of professional journalists has moved on.
13. It creates communities
Or, rather, communities form themselves around particular issues, people, events, artefacts, cultures, ideas, subjects or geographies. They may be temporary communities or long-terms ones, strong ones or weak ones. But they are recognisably communities.
14. It changes notions of authority
Instead of waiting to receive the “expert” opinions of others – mostly us journalists – Twitter shifts the balance to so-called “peer to peer” authority. It’s not that Twitterers ignore what we say – on the contrary (see distribution and marketing, above) they are becoming our most effective transmitters and responders. But, equally, we kid ourselves if we think there isn’t another force in play here – that a 21-year-old student is quite likely to be more drawn to the opinions and preferences of people who look and talk like her. Or a 31-year-old mother of young toddlers. Or a 41-year-old bloke passionate about politics and the rock music of his youth.
15. It is an agent of change
As this ability of people to combine around issues and to articulate them grows, so it will have increasing effect on people in authority. Companies are already learning to respect, even fear, the power of collaborative media. Increasingly, social media will challenge conventional politics and, for instance, the laws relating to expression and speech.
via The splintering of the fourth estate | Alan Rusbridger | Comment is free | guardian.co.uk.
-
Short, Sweet WP Video — Matt Mullenweg
A few months ago I was recently interviewed on KTEH’s program “This is Us!†and the result ended being a nice 5 minute overview of WordPress, something you could show to your Mom to explain the whole thing. Here’s the video (using Youtube’s new beta iframe player):
-
11 free ways to promote your website
Simple website promotional techniques can be undertaken by the business owner, or an appropriate employee, in the course of every day. Taking some of these actions, depending on the time you have available – in conjunction with a professional search engine optimisation strategy delivered by a digital media specialist – can really pay dividends.
-
Santander – Rapport Security Software feels like a Trojan
-
Oh well at least they’re honest

paypal unsubscribe This is the first time I’ve seen a promise that my unsubscribe request may get ignored for a week or so. I assume this means they have multiple spam databases and that they haven’t yet worked out how to keep them in sync in real time? I guess this is familiar territory for an industry that has insisted that it still takes as long as a pony can meander for a cheque to reach their clearing systems.
-
UXBrighton
Cennydd and James discuss the experience of writing a UX book, from the proposal and the money to the workflow and personal sacrifice involved. They talk about what publishers are looking for from potential authors, how to make a strong business case for your title, and how to come to terms with the alien practices of print publishing.
Cennydd and James will discuss the experience of writing a UX book, from the proposal and the money to the workflow and personal sacrifice involved. They’ll talk about what publishers are looking for from potential authors, how to make a strong business case for your title, and how to come to terms with the alien practices of print publishing.










